Windows Password Stealer
- BulletsPassView is a password recovery tool that reveals the passwords stored behind the bullets in the standard password text-box of Windows operating system and Internet Explorer Web browser. After revealing the passwords, you can easily copy them to the clipboard or save them into text/html/csv/xml file.
- PsPasswd is a tool that lets you change an account password on the local or remote systems, enabling administrators to create batch files that run PsPasswd against the computers they manage in order to perform a mass change of the administrator password. PsPasswd uses Windows password reset APIs, so does not send passwords over the network in the clear.
- Istealer is an efficient Windows Password Stealer software used to hack email account passwords. We have already reviewed how to use RATs and Trojans to hack email account passwords, which entails sending a keylogged file to your victim.
- USB password stealer is a USB flash disk or hard disk with scripts and tools used to collect password from the victim’s computer once connected. They use autorun.inf files to automate running the stealing tools, so to protect your computer you have to block running autorun.inf.
Now your USB password stealer is ready. All you have to do is insert it in your victims computer and a popup will appear, in the popup window select the option (Perform a virus scan) as soon as you will click it, your USB password stealer will do it’s magic and all the passwords saved on the system will be saved in a.txt file. PowerMemory: Credential Stealer Script For Wndows. PowerMemory is a powerful script which allows pen testers to extract user credentials present in memory and files. This handy script is developed by Pierre-Alexandre Braeken and it explains how to retrieve Windows credentials with Powershell and CDB Command-Line Options (Windows Debuggers).
Many people often tend to forget the WiFi password that they just used to login to a WiFi network on their Windows Computers. Thankfully, computers running Windows, store this password internally so that they can automatically log you in next time you are in that WiFi network’s range. But the real problem is faced when there are multiple networks that you can use and you need to use that password to log in from your other device as well. That other device may be an Android phone or an iPhone. These devices are not so tightly connected and integrated with a computer running Windows, that the password is synced automatically. Hence, the user faces difficulties in getting the WiFi password. But the developers at MagicJellyBean have come up with a simple solution. They call this WiFi Password Revealer.
With this tool, you can just check almost all the details bound to all the saved WiFi networks on your computer. These details include the SSID, Password, HEX Code, Authentication, Encryption as well as the type of connection. Let us now check out how we can use this tool to check the passwords of the saved WiFi networks.
WiFi Password Revealer & Finder software
The WiFi Password Revealer file weighs just 2.5 Megabytes. Once, downloaded, run the file by double-clicking on it. Hit Yes on the UAC prompt that you get.
Now, just follow the on-screen instructions as you install the software.
After it is done with the full installation, just run it either from an entry in the Start Menu or from a Shortcut on the desktop.
It will display all the information you need. You can click on the drop-down menu called view to show and hide data about the HEX Codes and the networks with empty passwords.
Extra Features and Points to Ponder
Some of the extra features and advantages this program provides a user with are as follows:
- It can decrypt passwords encrypted with WEP, WPA, WPA2, WPA-PSK,WPA2-PSK encryption techniques.
- It is totally compatible with a wide range of versions including the latest Windows 10.
- You can even use this with Windows Server.
- Works on systems with either of 32-bit or 64-bit architecture.
The developer has also listed some notes about the same. They are,
- To decrypt stored passwords on the machine you are scanning, you need to have Administrator rights.
- When the network has WPA encryption the retrieved password will be as 64 HEX digits. You can still use these characters like real password for internet connection.
You can download WiFi Password Revealer from here. It is not a Wi-Fi password sniffer or stealer. It will only show you your saved Wi-Fi passwords.
Want more? Here is a list of free Password Recovery tools to recover Windows, Browsers, Mail, Web, Wi-Fi, etc. passwords.
Related Posts:
Slacking on password security can have horrific consequences. Even so, it's easy to lose track of how many are vulnerable. With just a couple of files, you can steal passwords from nearly everywhere they're stored on a victim's Windows PC, including your own, just to see how secure they really are.
This post is part of our Evil Week series at Lifehacker, where we look at the dark side of getting things done. Knowing evil means knowing how to beat it, so you can use your sinister powers for good. Want more? Check out our evil week tag page.
Welcome to Lifehacker's Fifth Annual Evil Week
It's that time of year again: With Halloween getting closer, we're feeling the need to unleash our…
Read moreA good rule of thumb is that if you've stored a password on your computer, you've made it possible for someone else to steal with something as simple as a USB flash drive and a one-click script. This includes everything from wireless network keys to passwords you've saved in your browser. Hacker's Handbook has a great guide for the more experienced user, but we'll break it down for beginners here:
How to Hack Your Own Network and Beef Up Its Security with Kali Linux
Kali Linux is a security-focused operating system you can run off a CD or USB drive, anywhere.…
Read moreStep One: Collect Your Tools
NirSoft makes a ton of utilities that we love, and they have a pretty good suite of security tools. We're going to use a few that recover passwords to create our ultimate USB tool.
NirLauncher is the Ultimate Flash Drive Toolkit
Windows only: Portable application NirLauncher bundles 100+ of the best NirSoft utilities into a…
Swords and sandals 2 full version free. Pick up your weapon and fight for your life. Greater range of weapons, including ranged weapons. Swords and Sandals 2: Emperor's Reign features: The ability to save up to 10 characters.
Read morePlug in your USB drive, and create a folder titled 'Utilities'. Then, download the following zip files (not the self-install executables) from the NirSoft Password Recovery Utilities page onto the thumb drive and—after extracting the files—place all of the .exe files in the Utilities folder:
- MessenPass
- Mail PassView
- Protected Storage PassView
- Dialupass
- BulletsPassView
- Network Password Recovery
- SniffPass Password Sniffer
- RouterPassView
- PstPassword
- WebBrowserPassView
- WirelessKeyView
- Remote Desktop PassView
- VNCPassView
Each of these executable files recovers passwords from a specific place on the computer. For example, WirelessKeyView.exe pulls your wireless key, and WebBrowserPassView.exe grabs all of the passwords stored in your browsers. If you want to see what each one does in detail, check the NirSoft page linked above. If you see any other password recovery tools you want to try out, download them as well, but what we have here is a good starting point.
Step Two: Automate the Tools to Work With One Click (XP and Vista Only)
Next, we're going to set up a script that runs all these utilities at once—allowing you to grab a giant cache of stored passwords in one click (though it only works properly on Windows XP and Vista, so if you're only using this on Windows 7 and above, you can skip this step). Open your text editor, and for each file you downloaded, write this line of code in one text file:
Replace 'filename' with the name of the executable you just downloaded, including the file extension. When you replace 'filename' after the slash, you will change the .exe to a .txt file extension. This is the password log the executable will create for you to see. A finished script should look like this:
Once you're done writing the script, save the file as Launch.bat in the Utilities folder you created.
Step Three: Test Your New Password Stealer
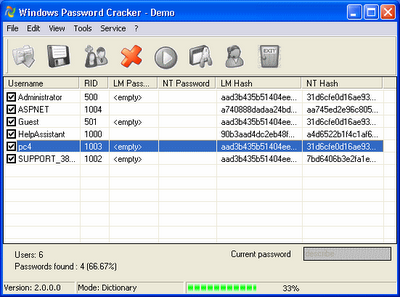
Now you will be able to recover the usernames and passwords from each of these programs. They will create detailed logs that show you the password, username, and source (like the Network name or website URL), which is all you really need to do damage. There's also the date the password was created, password strength, and other information depending on the program. Here's how to test your new password stealer to see how many passwords you've left vulnerable on your PC.
XP and Vista: Run the Script
Click the launch.bat file you just made to launch it. The password logs will appear in the Utilities folder as .txt files alongside the original executables. Each will have the same name as the .exe file they're sourced from. For example: the ChromePass.exe file will have a ChromePass.txt file that houses all of the recovered passwords and usernames. All you have to do is open the .txt files, and you'll see all your passwords.
Windows 7 and Above: Run Each Password Recovery App Individually
If you use Windows 7 or above, the script won't work for many of the apps, so you'll need to open them up individually. Double-click on each program and the list of passwords will pop up in a window. Select all that you want to save, and go to the File menu, and save the log as a .txt file in the original Utilities folder you created on your flash drive.
Use these logs to see for yourself how many passwords you've left vulnerable on your system. It's remarkably easy to find and take them!
Step Four: Protect Yourself
Now that you know how vulnerable your information is, get serious about protecting yourself. Take these precautions:
- If your computer has autorun enabled, disable it. It only takes a couple more lines of code to set the .bat file to launch automatically when the flash drive is plugged in, without the user even seeing what's happening.
- Take measures like not allowing your browser to remember your passwords, or at least the important ones like mobile banking. Instead, use password managers with encryption like LastPass or another good password manager to store all of your passwords securely and out of harm's way.
- Use two-factor authentication every chance you get. There are tons of ways for hackers to get your information if they want to. The second factor—something you have—could be what saves you in the end.
- The obvious: always maintain physical control of your computer whenever possible. Never leave your PC unattended with anyone else, especially someone who's using a USB flash drive. In fact, it wouldn't hurt to offer to do the work yourself as often as possible when a friend asks if they can use your computer.
Strong passwords aren't all the protection you need. Understand how vulnerable your information really is, and build a nearly hack-proof password system to stay safe.
How to Build a (Nearly) Hack-Proof Password System with LastPass and a Thumb Drive
It seems like every day there's news that a new site or service has been hacked. The intruders…
Read morePassword Stealer Download
Photos by SamahR, Chris Yarzab, and Ervins Strauhmanis.